找了一道题来做,是2018强网杯的core,这道题因为当时不会kernel pwn,所以没做,现在来回顾一下
首先可以提取出core.ko,详细的功能我这里也不多做描述
因为kernel 开了canary 所以首先要leak出来
然后/proc/kallsyms 在初始化的时候也复制到/tmp/kallsyms,所以可以直接得到prepare_kernel_cred 和commit_creds的地址
然后驱动的漏洞的话是在core_copy_func这个函数里面,比较的时候没有截断,但是复制的时候截断了,所以可以构造一个没有截断前是负数,截断后是一个正数的数字,这样就能造成栈溢出

rop调用完commit_creds(prepare_kernel_cred (0));
然后要返回用户空间,这里坑得有点久,要用1
2swapgs
iretq
这两个指令,然后就能返回到用户空间,拿到root shell
还有一个坑就是,不能从带符号的vmlinux里面找gadget,要从bzImage里面提取之后再找gadget
下面是我的poc,编译命令是gcc poc.c -o poc -static -masm=intel
1 | #include <stdio.h> |
运行结果
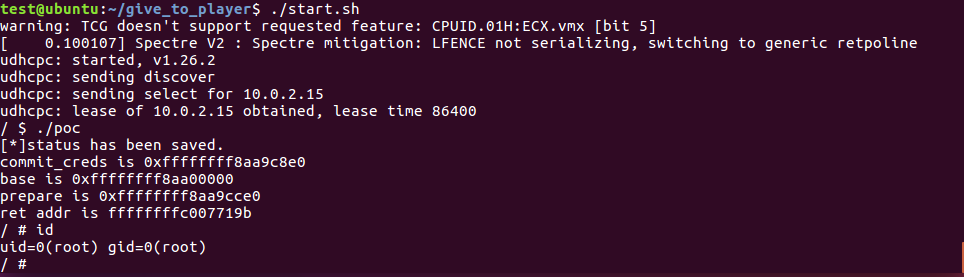
下面还有另外一个poc,这个只是改了一下,把base的获取从/proc/kallsyms拿变成leak 栈上的内容,leak完之后减去偏移,得到base
1 | #include <stdio.h> |